White Hat Hacking involves ethical hackers using their skills to identify security vulnerabilities and strengthen systems against potential threats. Black Hat Hacking focuses on exploiting weaknesses for malicious purposes, such as data theft or system disruption. Understanding the contrasting motives and techniques between White Hat and Black Hat hacking is essential for developing robust cybersecurity strategies.
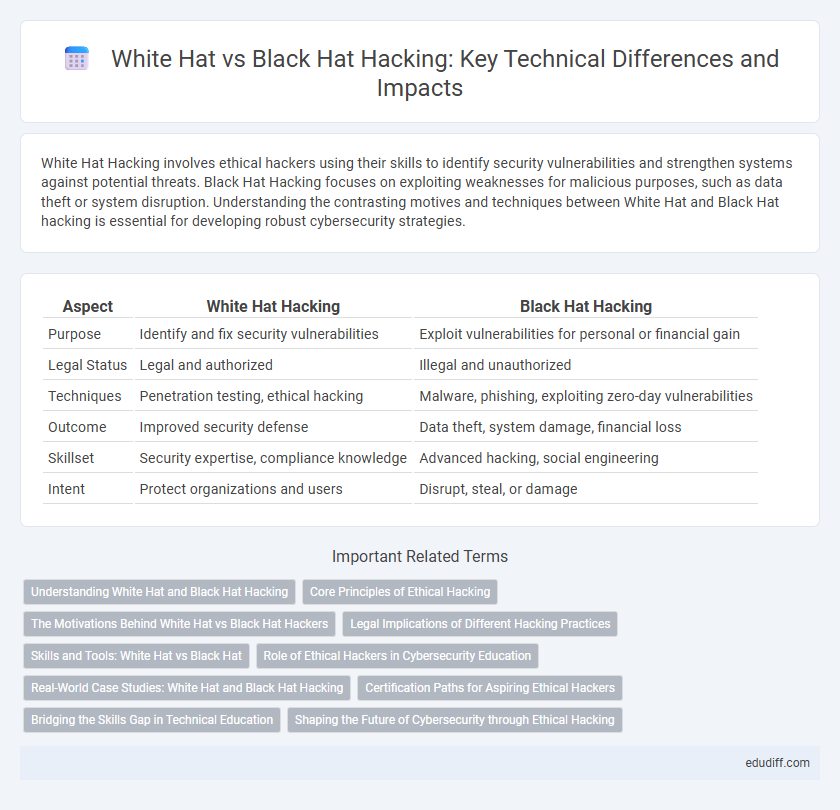
Table of Comparison
| Aspect | White Hat Hacking | Black Hat Hacking |
|---|---|---|
| Purpose | Identify and fix security vulnerabilities | Exploit vulnerabilities for personal or financial gain |
| Legal Status | Legal and authorized | Illegal and unauthorized |
| Techniques | Penetration testing, ethical hacking | Malware, phishing, exploiting zero-day vulnerabilities |
| Outcome | Improved security defense | Data theft, system damage, financial loss |
| Skillset | Security expertise, compliance knowledge | Advanced hacking, social engineering |
| Intent | Protect organizations and users | Disrupt, steal, or damage |
Understanding White Hat and Black Hat Hacking
White Hat hacking involves authorized cybersecurity professionals who use their skills to identify and fix security vulnerabilities, ensuring systems remain protected from malicious threats. Black Hat hacking refers to unauthorized individuals exploiting security weaknesses for personal gain, causing data breaches, financial loss, and damage to organizational reputation. Understanding these contrasting roles is crucial for developing effective cybersecurity strategies and promoting ethical hacking practices.
Core Principles of Ethical Hacking
White Hat Hacking centers on authorized security assessments aimed at identifying and fixing vulnerabilities to protect systems, emphasizing legality, confidentiality, and integrity. Ethical hackers adhere to strict protocols ensuring all activities are consented to and documented, reinforcing trust and compliance with cybersecurity laws. The core principles include proactive defense, risk management, and safeguarding user data against malicious exploitation typical of Black Hat Hacking.
The Motivations Behind White Hat vs Black Hat Hackers
White Hat hackers are primarily motivated by the desire to improve cybersecurity by identifying and fixing vulnerabilities before malicious actors can exploit them. In contrast, Black Hat hackers pursue financial gain, data theft, or disruption by exploiting system weaknesses for personal or ideological benefits. White Hat motivations align with ethical standards and legal frameworks, while Black Hat objectives often involve unauthorized access and harm to digital infrastructures.
Legal Implications of Different Hacking Practices
White hat hacking operates within legal boundaries by obtaining proper authorization to identify and fix security vulnerabilities, ensuring compliance with laws like the Computer Fraud and Abuse Act (CFAA). In contrast, black hat hacking involves unauthorized access to systems, leading to criminal charges, civil liabilities, and severe penalties under cybersecurity laws worldwide. The distinction between ethical hacking and malicious hacking hinges on consent, intent, and adherence to regulatory frameworks governing information security.
Skills and Tools: White Hat vs Black Hat
White Hat hackers utilize advanced penetration testing tools, vulnerability scanners, and ethical hacking frameworks such as Metasploit and Wireshark to identify and fix security flaws legally. Black Hat hackers employ similar technical skills but leverage exploit kits, malware, and social engineering techniques to breach systems illicitly and cause damage or steal data. The core distinction lies in the intent and application of skills: White Hats prioritize system protection, while Black Hats focus on exploitation.
Role of Ethical Hackers in Cybersecurity Education
Ethical hackers, also known as white hat hackers, play a crucial role in cybersecurity education by simulating real-world cyberattacks to identify vulnerabilities in systems before malicious actors exploit them. Their expertise provides hands-on training for security professionals and raises awareness about effective countermeasures against black hat hacking techniques. Integrating ethical hacking into cybersecurity curricula enhances practical skills, promotes responsible hacking behavior, and strengthens overall defense mechanisms against cyber threats.
Real-World Case Studies: White Hat and Black Hat Hacking
White hat hacking involves ethical cybersecurity experts who identify system vulnerabilities to enhance defense mechanisms, exemplified by companies like Google employing bug bounty programs to uncover and fix security flaws. In contrast, black hat hackers exploit these vulnerabilities for malicious gains, illustrated by the 2017 Equifax breach where attackers accessed sensitive data affecting 147 million individuals. Real-world case studies emphasize that proactive white hat interventions can prevent devastating attacks, whereas black hat activities often result in significant financial and reputational damage to organizations.
Certification Paths for Aspiring Ethical Hackers
White Hat Hacking certification paths include CEH (Certified Ethical Hacker), OSCP (Offensive Security Certified Professional), and CISSP (Certified Information Systems Security Professional), each emphasizing legal and ethical penetration testing skills. Black Hat Hacking lacks formal certification as it involves unauthorized and illegal activities, posing significant legal risks and ethical violations. Aspiring ethical hackers are strongly recommended to pursue recognized certifications to validate their expertise and adhere to cybersecurity industry standards.
Bridging the Skills Gap in Technical Education
White Hat Hacking and Black Hat Hacking represent contrasting approaches to cybersecurity, with ethical hackers focusing on protecting systems while malicious hackers exploit vulnerabilities. Bridging the skills gap in technical education requires integrating real-world ethical hacking practices, hands-on training programs, and updated curricula that emphasize defensive strategies and cybersecurity principles. Empowering students with practical White Hat Hacking skills strengthens organizational security and addresses the growing demand for proficient cybersecurity professionals.
Shaping the Future of Cybersecurity through Ethical Hacking
White Hat Hacking employs authorized techniques to identify and fix security vulnerabilities, strengthening cybersecurity defenses and preventing malicious breaches. Black Hat Hacking exploits system weaknesses for illegal activities, posing significant threats to data integrity and privacy. Ethical hacking shapes the future of cybersecurity by promoting proactive risk mitigation, advancing vulnerability assessment methodologies, and fostering a culture of cyber resilience.
White Hat Hacking vs Black Hat Hacking Infographic
 edudiff.com
edudiff.com